Hello friends, in this article I am showing that how to create fake contact no. to run WhatsApp account with fake contact no. Previous days, an application named VOXOX was working very well to create fake contact no. but from many days this app is not working due to their policies. I am showing you here that how to create fake contact no. of Philippines with starting +63 xxx xxx xxxx. If you want to create a fake contact no. of USA with starting +1(xxx)xxx-xxxx then read this articles. Now read below carefully.
REQUIREMENTS:
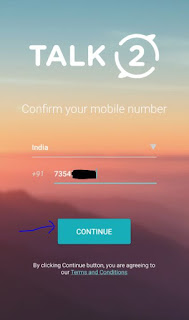
STEP 2: Press on CONFIRM NUMBER A confirmation code will sent to your no. to verify. Verify it.
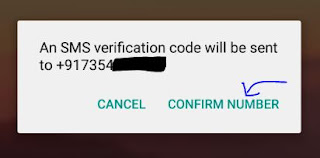
STEP 3: After verifying, click on CONTINUE.

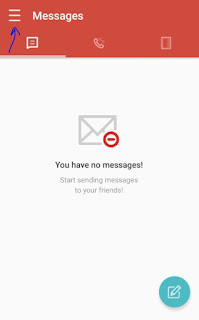
STEP 4: Click on MENU (i.e., 3 lines).
STEP 5: Now see you have created fake contact no.
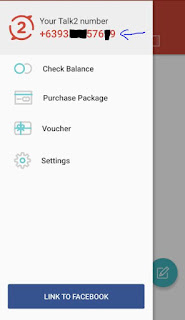
Congratulations, you have made fake contact no. to run WhatsApp, hike, etc. whatever you want. But friends, it is little bit tough to create WhatsApp account with this app. So if you want to create fake WhatsApp no. then click here to read.
Don’t forget to share with your friends as I am sharing to you because sharing is caring. Thanks…….
REQUIREMENTS:
- Talk2 DOWNLOAD
- Patience ☺
- Follow these steps simply. It’s not tough as you are thinking.

STEP 2: Press on CONFIRM NUMBER A confirmation code will sent to your no. to verify. Verify it.

STEP 3: After verifying, click on CONTINUE.

STEP 4: Click on MENU (i.e., 3 lines).

STEP 5: Now see you have created fake contact no.

Congratulations, you have made fake contact no. to run WhatsApp, hike, etc. whatever you want. But friends, it is little bit tough to create WhatsApp account with this app. So if you want to create fake WhatsApp no. then click here to read.
Don’t forget to share with your friends as I am sharing to you because sharing is caring. Thanks…….
Comments